#mongodb centos install yum
Explore tagged Tumblr posts
Text
Install MongoDB on CentOS 7 Linux Step by Step.
Install MongoDB on CentOS 7 Linux Step by Step.
We will see How to Install MongoDB on CentOS 7 Linux Step by Step, MongoDB is a No-SQL database that is written in C++, It uses a JSON-like structure. MongoDB is a cross-platform and document-oriented database. The initial release of the MongoDB was on 11 February 2009, you can find the main website of the MongoDB as well the git repository So let’s install MongoDB on CentOS 7 Linux Step by…
View On WordPress
#install mongodb#install mongodb centos 7#install mongodb centos 7.5#install mongodb on centos 7#install mongodb on linux#install mongodb on ubuntu#mongodb centos install yum#mongodb install centos#mongodb install linux
0 notes
Text
All applications generate information when running, this information is stored as logs. As a system administrator, you need to monitor these logs to ensure the proper functioning of the system and therefore prevent risks and errors. These logs are normally scattered over servers and management becomes harder as the data volume increases. Graylog is a free and open-source log management tool that can be used to capture, centralize and view real-time logs from several devices across a network. It can be used to analyze both structured and unstructured logs. The Graylog setup consists of MongoDB, Elasticsearch, and the Graylog server. The server receives data from the clients installed on several servers and displays it on the web interface. Below is a diagram illustrating the Graylog architecture Graylog offers the following features: Log Collection – Graylog’s modern log-focused architecture can accept nearly any type of structured data, including log messages and network traffic from; syslog (TCP, UDP, AMQP, Kafka), AWS (AWS Logs, FlowLogs, CloudTrail), JSON Path from HTTP API, Beats/Logstash, Plain/Raw Text (TCP, UDP, AMQP, Kafka) e.t.c Log analysis – Graylog really shines when exploring data to understand what is happening in your environment. It uses; enhanced search, search workflow and dashboards. Extracting data – whenever log management system is in operations, there will be summary data that needs to be passed to somewhere else in your Operations Center. Graylog offers several options that include; scheduled reports, correlation engine, REST API and data fowarder. Enhanced security and performance – Graylog often contains sensitive, regulated data so it is critical that the system itself is secure, accessible, and speedy. This is achieved using role-based access control, archiving, fault tolerance e.t.c Extendable – with the phenomenal Open Source Community, extensions are built and made available in the market to improve the funmctionality of Graylog This guide will walk you through how to run the Graylog Server in Docker Containers. This method is preferred since you can run and configure Graylog with all the dependencies, Elasticsearch and MongoDB already bundled. Setup Prerequisites. Before we begin, you need to update the system and install the required packages. ## On Debian/Ubuntu sudo apt update && sudo apt upgrade sudo apt install curl vim git ## On RHEL/CentOS/RockyLinux 8 sudo yum -y update sudo yum -y install curl vim git ## On Fedora sudo dnf update sudo dnf -y install curl vim git 1. Install Docker and Docker-Compose on Linux Of course, you need the docker engine to run the docker containers. To install the docker engine, use the dedicated guide below: How To Install Docker CE on Linux Systems Once installed, check the installed version. $ docker -v Docker version 20.10.13, build a224086 You also need to add your system user to the docker group. This will allow you to run docker commands without using sudo sudo usermod -aG docker $USER newgrp docker With docker installed, proceed and install docker-compose using the guide below: How To Install Docker Compose on Linux Verify the installation. $ docker-compose version Docker Compose version v2.3.3 Now start and enable docker to run automatically on system boot. sudo systemctl start docker && sudo systemctl enable docker 2. Provision the Graylog Container The Graylog container will consist of the Graylog server, Elasticsearch, and MongoDB. To be able to achieve this, we will capture the information and settings in a YAML file. Create the YAML file as below: vim docker-compose.yml In the file, add the below lines: version: '2' services: # MongoDB: https://hub.docker.com/_/mongo/ mongodb: image: mongo:4.2 networks: - graylog #DB in share for persistence volumes: - /mongo_data:/data/db # Elasticsearch: https://www.elastic.co/guide/en/elasticsearch/reference/7.10/docker.html
elasticsearch: image: docker.elastic.co/elasticsearch/elasticsearch-oss:7.10.2 #data folder in share for persistence volumes: - /es_data:/usr/share/elasticsearch/data environment: - http.host=0.0.0.0 - transport.host=localhost - network.host=0.0.0.0 - "ES_JAVA_OPTS=-Xms512m -Xmx512m" ulimits: memlock: soft: -1 hard: -1 mem_limit: 1g networks: - graylog # Graylog: https://hub.docker.com/r/graylog/graylog/ graylog: image: graylog/graylog:4.2 #journal and config directories in local NFS share for persistence volumes: - /graylog_journal:/usr/share/graylog/data/journal environment: # CHANGE ME (must be at least 16 characters)! - GRAYLOG_PASSWORD_SECRET=somepasswordpepper # Password: admin - GRAYLOG_ROOT_PASSWORD_SHA2=e1b24204830484d635d744e849441b793a6f7e1032ea1eef40747d95d30da592 - GRAYLOG_HTTP_EXTERNAL_URI=http://192.168.205.4:9000/ entrypoint: /usr/bin/tini -- wait-for-it elasticsearch:9200 -- /docker-entrypoint.sh networks: - graylog links: - mongodb:mongo - elasticsearch restart: always depends_on: - mongodb - elasticsearch ports: # Graylog web interface and REST API - 9000:9000 # Syslog TCP - 1514:1514 # Syslog UDP - 1514:1514/udp # GELF TCP - 12201:12201 # GELF UDP - 12201:12201/udp # Volumes for persisting data, see https://docs.docker.com/engine/admin/volumes/volumes/ volumes: mongo_data: driver: local es_data: driver: local graylog_journal: driver: local networks: graylog: driver: bridge In the file, replace: GRAYLOG_PASSWORD_SECRET with your own password which must be at least 16 characters GRAYLOG_ROOT_PASSWORD_SHA2 with a SHA2 password obtained using the command: echo -n "Enter Password: " && head -1 1514/tcp, :::1514->1514/tcp, 0.0.0.0:9000->9000/tcp, 0.0.0.0:1514->1514/udp, :::9000->9000/tcp, :::1514->1514/udp, 0.0.0.0:12201->12201/tcp, 0.0.0.0:12201->12201/udp, :::12201->12201/tcp, :::12201->12201/udp thor-graylog-1 1a21d2de4439 docker.elastic.co/elasticsearch/elasticsearch-oss:7.10.2 "/tini -- /usr/local…" 31 seconds ago Up 28 seconds 9200/tcp, 9300/tcp thor-elasticsearch-1 1b187f47d77e mongo:4.2 "docker-entrypoint.s…" 31 seconds ago Up 28 seconds 27017/tcp thor-mongodb-1 If you have a firewall enabled, allow the Graylog service port through it. ##For Firewalld sudo firewall-cmd --zone=public --add-port=9000/tcp --permanent sudo firewall-cmd --reload ##For UFW sudo ufw allow 9000/tcp 5. Access the Graylog Web UI Now open the Graylog web interface using the URL http://IP_address:9000. Log in using the username admin and SHA2 password(StrongPassw0rd) set in the YAML. On the dashboard, let’s create the first input to get logs by navigating to the systems tab and selecting input. Now search for Raw/Plaintext TCP and click launch new input Once launched, a pop-up window will appear as below. You only need to change the name for the input, port(1514), and select the node, or “Global” for the location for the input. Leave the other details as they are. Save the file and try sending a plain text message to the Graylog Raw/Plaintext TCP input on port 1514. echo 'First log message' | nc localhost 1514 ##OR from another server##
echo 'First log message' | nc 192.168.205.4 1514 On the running Raw/Plaintext Input, show received messages The received message should be displayed as below. You can as well export this to a dashboard as below. Create the dashboard by providing the required information. You will have the dashboard appear under the dashboards tab. Conclusion That is it! We have triumphantly walked through how to run the Graylog Server in Docker Containers. Now you can monitor and access logs on several servers with ease. I hope this was significant to you.
0 notes
Text
How to install gdb on centos

#HOW TO INSTALL GDB ON CENTOS HOW TO#
#HOW TO INSTALL GDB ON CENTOS INSTALL#
#HOW TO INSTALL GDB ON CENTOS SOFTWARE#
#HOW TO INSTALL GDB ON CENTOS FREE#
> Processing Dependency: devtoolset-7-runtime for package: devtoolset-7-gcc-7.3.1-5.4.el7.x86_64
#HOW TO INSTALL GDB ON CENTOS INSTALL#
Here is the output in our ~]# yum install devtoolset-7-gcc* STEP 2) Install the development tools and GNU GCC 7, which is part of the “devtools” package > Package centos-release-scl-rh.noarch 0: will be installedĬentos-release-scl noarch extras 12 kĬentos-release-scl-rh noarch extras 12 k > Processing Dependency: centos-release-scl-rh for package: > Package centos-release-scl.noarch 0: will be installed Loading mirror speeds from cached hostfile Here is the output in our ~]# yum -y install centos-release-scl
#HOW TO INSTALL GDB ON CENTOS HOW TO#
So here is how to install GNU GCC 7: STEP 1) Install the repository in your system This article is to install GNU GCC 7 on CentOS 7 and we have a new one to install GNU GCC 8 – How to install GNU GCC 8 on CentOS 7. To have a newer version of the same components, you can have multiple version of GNU GCC – you can install with no worries of breaking your system GNU GCC 6 and 7.Not only GNU GCC, but you can also have PHP, Ruby, Python, famous databases like Mysql, MongoDB, PostgreSQL and many more Multiple version installed of the same components, you can have multiple GNU GCC installed without breaking your system or compiling manually.We can say these packages are officially maintained by CentOS 7 team and as a whole Red Hat/CentOS officials and community developers! The collection aims at
#HOW TO INSTALL GDB ON CENTOS SOFTWARE#
There are repositories, which would surely break your system at one point even they do not break it at first installing a newer version of GNU GCC! There is a really easy and “official” way to have newer development software in CentOS 7 by using the Software Collection –
#HOW TO INSTALL GDB ON CENTOS FREE#
It offers us free enterprise-class operating system, which is compatible with Red Hat, but in many situations, we need a newer (not even a bleeding edge) tools from a trusted source not from an unknown third repository! Let’s say you are a developer and you need newer than GCC 4.8 (which is more than 5 years old and at present, we have stable GCC 8.x stable branch). In order to close this display screen, you need to use the following combination: CTRL + A + D.CentOS 7 is a very stable and conservative operating system. In order for it to be available for the entire system, we will need to run the following command: make install Configuring CPULimit Using the Applicationīy entering the special top command it is possible to view the list of processes. When this process completes, a binary file will appear in the cpulimit-2.5 directory. The next step is to run make to start compiling CPULimit: make The next step is to run make to start compiling CPULimit: cd cpulimit-2.5 Then you need to install and, therefore, unpack the archive: cd ~ To quickly and successfully install this utility, you need make, screen, and wget. Some applications that may be limited include Nginx, PHP, Java. It is worth noting here that most applications will run normally. Essentially, applications will turn on or off quickly enough to limit the program to the desired number of cycles. It works as follows: CPULimit is not designed to work with applications that use job control, for example as they can be destroyed when CPULimit sends the SIGSTOP stop signal. One of the important differences is that cpulimit does not manage system boot, unlike cputool. Cpulimit is used to limit the CPU usage of a process in the same way as CPUTool, however it offers more use cases than its counterpart. CPULimit is a utility designed to work with Linux servers to limit the use of resources by an application.

0 notes
Text
How to Install MongoDB Community Edition on Linux
How to Install MongoDB Community Edition on Linux
Install MongoDB Community Edition on Linux MongoDB provides packages for common Linux systems for the best installation experience. The recommended approach to run MongoDB is using these packages. The following guidelines will walk you through the installation of these systems: Install MongoDB Community Edition on Red Hat or CentOS Using the yum package manager, install MongoDB 5.0 Community…

View On WordPress
0 notes
Link
MongoDB is a NoSQL database that is designed to store large data amounts in document-oriented storage with a dynamic schema. Install MongoDB centos 7 is the leading NoSQL database used in modern web applications.
0 notes
Text
Montar un servidor web con OneinStack

Montar un servidor web con OneinStack. OneinStack es paquete en formato de script que nos permite crear diversos tipos de servidor web en Linux, y todo sin necesidad de tener grandes conocimientos. Con OeinStack podemos crear de manera sencilla los siguientes entornos: Lnmp / Lemp(Linux + Nginx+ MySQL/MongoDB+ PHP) Lamp(Linux + Apache+ MySQL/MongoDB+ PHP) Lnmpa (Linux + Nginx+ MySQL/MongoDB+ PHP+ Apache): Nginx handles static, Apache handles dynamic PHP Lnmt (Linux + Nginx+ MySQL/MongoDB+ Tomcat): Nginx handles static, Tomcat (JDK) handles JAVA Lnpp(Linux + Nginx+ PostgreSQL+ PHP) Lapp(Linux + Apache+ PostgreSQL+ PHP) Lnmh(Linux + Nginx+ MySQL+ HHVM) Es compatible con las siguientes distribuciones linux y sus derivados: CentOS 6-7 Debian 8-10 Ubuntu 14-19 Fedora 27+ Deepin 15 Amazon Linux 2 Aliyun Linux El paquete se mantiene constantemente actualizado desde el código fuente original, hoy día 15 de Julio del 2019 estas son las versiones disponibles que puedes instalar. # Web # DB # PHP nginx_ver=1.16.0 mysql80_ver=8.0.16 php73_ver=7.3.7 tengine_ver=2.3.0 mysql57_ver=5.7.26 php72_ver=7.2.20 openresty_ver=1.15.8.1 mysql56_ver=5.6.44 php71_ver=7.1.30 apache24_ver=2.4.39 mysql55_ver=5.5.62 php70_ver=7.0.33 apache22_ver=2.2.34 mariadb104_ver=10.4.6 php56_ver=5.6.40 tomcat9_ver=9.0.20 mariadb103_ver=10.3.16 php55_ver=5.5.38 tomcat8_ver=8.5.41 mariadb102_ver=10.2.25 php54_ver=5.4.45 tomcat7_ver=7.0.94 mariadb55_ver=5.5.64 php53_ver=5.3.29 tomcat6_ver=6.0.53 percona80_ver=8.0.15-6 # JDK percona57_ver=5.7.26-29 jdk110_ver=11.0.2 percona56_ver=5.6.44-86.0 jdk18_ver=1.8.0_212 percona55_ver=5.5.62-38.14 jdk17_ver=1.7.0_80 alisql56_ver=5.6.32-9 jdk16_ver=1.6.0_45 pgsql_ver=11.4 mongodb_ver=4.0.10 # phpMyAdmin # Jemalloc # Pure-FTPd phpmyadmin_ver=4.8.5 jemalloc_ver=5.2.0 pureftpd_ver=1.0.49 phpmyadmin_oldver=4.4.15.10 # Redis # Memcached redis_ver=5.0.5 memcached_ver=1.5.16 Vemos como instalar un servidor web con OneinStack.
Montar un servidor web con OneinStack
Necesitamos tener instalado "wget" y "screen", en el ejemplo sobre CentOS y Ubuntu. En CentOS: sudo yum -y install wget screen En Ubuntu: sudo apt-get -y install wget screen Descargamos el paquete (desde una de las dos propuestas siguientes). wget http://mirrors.linuxeye.com/oneinstack-full.tar.gz wget http://downloads.sourceforge.net/project/oneinstack/oneinstack-full.tar.gz Una vez descargado lo descomprimimos. tar xzf oneinstack-full.tar.gz Accedemos a la carpeta generada. cd oneinstack Ahora comenzamos la installation, para ello ejecutamos el script. sudo ./install.sh Veremos un asistente en línea de comandos que nos ayudara a configurar nuestro servidor web de manera simple, según nuestras necesidades. Servidor Nginx, Apache y Tomcat Selecciona entre las opciones propuestas.
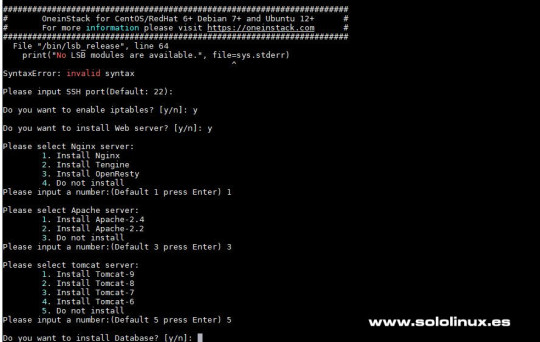
Instalar un servidor web con OneinStack Servidor de base de datos Selecciona que database server quieres utilizar e introduces una contraseña de root.
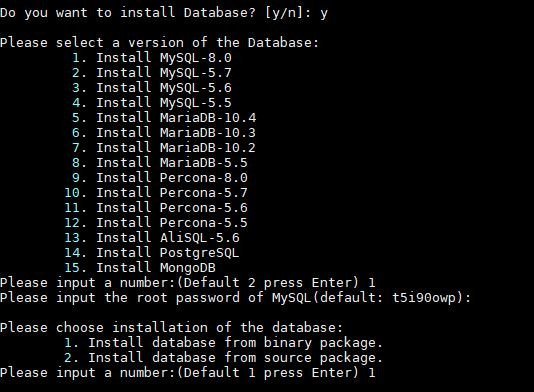
Instalar base de datos en Oneinstack Seleccionamos la version PHP a instalar Ahora, nos pregunta qué versión de PHP queremos configurar en nuestro servidor web. Además del PHP, el script OneinStack nos ofrece la opción de configurar un sistema de caché, selecciona entre Zend OPcache y APCU. Tanbién podemos instalar las extensiones de php que vayamos a necesitar, por defecto se instalan las extensiones 4, 11, 12. Si no está seguro pulsa Intro para instalar las extensiones predeterminadas.

Instalar version de php en Oneinstack Aplicaciones varias Tal vez te interese instalar aplicaciones como Pure-FTPd, PhpMyAdmin, redis-server, memcached-server o HHVM.
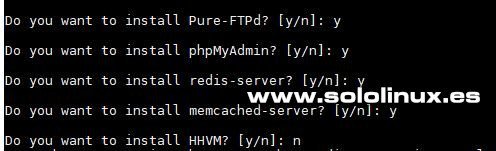
Instalar FTP HHVM redis memcached en OneinStack Una vez tengamos nuestra selección realizada comienza a instalarse el server, ten en cuenta que dependiendo de tu conexión a internet puede tardar más o menos. Panel de control OneinStack Ya hemos terminado de montar nuestro servidor web, ahora podemos acceder desde nuestro navegador web favorito simplemente introduciendo la ip. Desde el panel de control podrás acceder a todas las opciones.
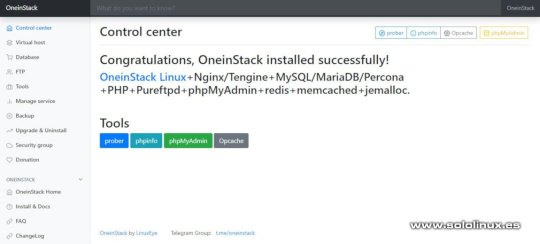
Panel de control Oneinstack Instalar complementos Podemos instalar PHP composer, fail2ban, ngx_lua_waf y Python3.6. cd oneinstack sudo ./addons.sh
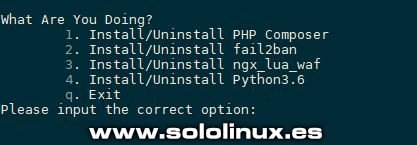
Instalar Add ons en OneinStack Crear certificado Let’s Encrypt Si quieres algún dominio en el servidor agregas la dirección IP del sistema en un registro A de las DNS del dominio. Después ejecuta lo siguiente... sudo ./vhost.sh Sigue los pasos que te aparecen en pantalla.
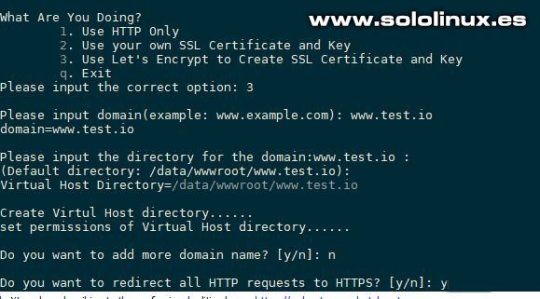
Instalar lets crypt SSL en OneinStack Si quieres borrar el host virtual. vhost.sh --del Espero que este articulo te sea de utilidad, puedes colaborar con nosotros con el simple gesto de compartir los artículos en tu sitio web, blog, foro o redes sociales. Read the full article
#15deJuliodel2019#Apache#APCU#distribucioneslinux#lamp#LAPP#LEMP#LNMH#lnmp#LNMPA#LNMT#LNPP#Montarunservidorweb#oneinstack#script#scriptOneinStack#servidor#ServidorNginx#servidorweb#tomcat#wget#Zendopcache
0 notes
Text
10 Basic Strides for Planning Another Laborer
By Tres Logics
That is a respectable new Linux laborer you showed up at… it would be a shame if something some way or another figured out how to happen to it. It might drive okay to leave the holder, yet before you put it in progress, there are 10 phases you need to take to guarantee it's planned securely. The nuances of these methods may change starting with one scattering then onto the next, yet sensibly they apply to any sort of Linux. By affirming these methods on new specialists, you can ensure that they have in any occasion fundamental protection from the most broadly perceived attacks.
What Why
Customer configuration Secure your accreditations
Association configuration Build up correspondences
Pack management Add what you need, wipe out what you don't
Update installation Fix your shortcomings
NTP configuration Forestall clock drift
Firewalls and Iptables Limit your external impression
Getting SSH Solidify far away gatherings
Daemon configuration Minimize your attack surface
SELinux and further hardening Protect the piece and applications
Logging Know what's happening
1 - Customer Game plan
Indisputably the main thing you should do if it wasn't fundamental for your working framework game plan, is to change the root secret key. This should act normally obvious anyway can be incredibly overlooked during an ordinary laborer course of action. The mysterious word should be at any rate 8 characters, using a blend of upper and lowercase letters, numbers, and pictures. You should in like manner set up a mysterious key procedure that decides developing, locking, history, and unpredictability necessities if you will use close by records. A large part of the time, you ought to debilitate the root customer through and through and make non-supported customer accounts with sudo access for the people who require raised rights.
2 - Association Plan
Maybe the most fundamental arrangements you'll need to make is to engage network accessibility by distributing the specialist an IP address and hostname. For most laborers, you'll need to use a static IP so clients can by and large find the resource at a comparative area. If your association uses VLANs, consider how disconnected the specialist's section is and where it would best fit. In case you don't use IPv6, turn it off. Set the hostname, region, and DNS specialist information. At any rate two DNS laborers should be used for overabundance and you should test ns-lookup to guarantee the name objective is working adequately.
3 - Pack The chiefs
Presumably, you're setting up your new specialist for a specific explanation, so guarantee you present whatever groups you may need if they aren't fundamental for the scattering you're using. These could be application packs like PHP, MongoDB, Nginx or supporting groups like a pear. Essentially, any coincidental groups that are acquainted on your structure should with be taken out to wither the specialist impression. The whole of this should be done through your movement's pack the board game plan, for instance, yum or capable for less complex organization so to speak.
4 - Update Foundation and Plan
At the point when you have the right packages presented on your laborer, you ought to guarantee everything is revived. The groups you presented, yet the part and default packages as well. But in the event that you have a need for a specific structure, you should reliably use the latest creation conveyance to keep your system secure. Ordinarily, your pack the chief's plan will pass on the most state-of-the-art maintained variation. You should in like manner consider setting up modified revives inside the group the board instrument if doing so works for the service(s) you're working with on this laborer
5 - NTP Game plan
Mastermind your specialist to synchronize its chance with NTP laborers. These could be inside NTP laborers if your present condition has those or outside miscreants that are open for anyone. What's critical is to prevent clock skim, where the laborer's clock inclines from the constant. This can cause a huge load of issues, including approval issues where the time incline between the laborer and the affirming establishment is assessed before surrendering access. This should be a fundamental change, yet it's an essential piece of a strong system.
6 - Firewalls and iptables
Dependent upon your movement, iptables may as of now be completely gotten and anticipate that you should open what you need, anyway paying little psyche to the default config, you should reliably explore it and guarantee it's set up the way where you need. Try to reliably use the norm of least benefit and simply open those ports you thoroughly need for the organizations on that laborer. If your specialist is behind a submitted firewall or something to that effect, make sure to deny everything aside from what's significant there as well. Tolerating your iptables/firewall IS restrictive as per usual, make sure to open up what you need for your specialist to handle its work!
7 - Getting SSH
SSH is the rule far away access method for Linux courses and as such should be fittingly gotten. You ought to incapacitate the root's ability to SSH in indirectly, whether or not you injured the record with the objective that just in case of root gets enabled on the specialist for no good reason it really will not be exploitable remotely. You can similarly restrict SSH to certain IP ranges if you have a fixed course of action of client IPs that will interface. On the other hand, you can change the default SSH port to "dull" it, yet really, a fundamental yield will uncover the new open port to any person who needs to find it. Finally, you can disable mystery express check completely and use confirmation based affirmation to decrease extensively further the chances of SSH misuse.
8 - Daemon Arrangement
You've cleaned up your packs, and yet, it's basic to set the right applications to AutoStart on reboot. Make sure to execute any daemons you needn't mess with. One key to a protected specialist is decreasing the unique impression whatever amount as could be anticipated so the solitary surface districts available for attack are those required by the application(s). At whatever point this is done, lingering organizations should be cemented whatever amount as could be required to ensure strength.
9 - SELinux and Further Cementing
In case you've anytime used a Red Cap distro, you might be familiar with SELinux, the bit setting gadget that safeguards the system from various errands. SELinux is unprecedented at getting against unapproved use and access of structure resources. It's in like manner inconceivable at breaking applications, so guarantee you test your plan out with SELinux enabled and use the logs to guarantee nothing certifiable is being obstructed. Past this, you need to explore setting any applications like MySQL or Apache, as everybody will have a set-up of best practices to follow.
10 - Logging
Finally, you ought to guarantee that the level of logging you need is enabled and that you have sufficient resources for it. You will end up examining this specialist, so assist yourself with excursion and collect the logging structure you'll need to deal with issues quickly. Most programming has configurable logging, nonetheless, you'll require some experimentation to find the right concordance between inadequate information and to a limit. There are a huge gathering of pariah logging instruments that can help including combination to portrayal, yet every environment ought to be considered for its necessities first. By then, you can find the tool(s) that will help you fill them.
Each and every one of these methods can save some push to complete, especially the initial go through around. In any case, by setting up an ordinary act of starting laborer course of action, you can ensure that new machines in your present situation will be adaptable. Failure to take any of these steps can incite truly real results if your laborer is ever the target of an attack. Following them won't guarantee prosperity - data infiltrates happen - yet it makes it certainly harder for malignant performers and will require some degree of capacity to endure.
Worker Setup By Tres Logics
We have a solid group of specialists in the field of various Worker solidifying Establishment/setup, the board, and support.
We offer types of assistance in the accompanying regions:
Cloud Worker Establishments/Arrangement, The executives, support, and organizations. (MS Sky blue, AWS, and so forth)
Linux Worker Establishment, The board, and Support (Ubuntu, RedHat, CentOS, and so forth)
Window Workers (2016 ,2012 ,2008)
Linux, Apache, MySQL, and PHP (Light) Arrangement and Upkeep
Control Board Establishment/arrangement, the executives, and support (cPanel, Plesk, CentOS Web Board).
Java Worker Climate arrangement (Apache Tomcat, JBoss EAP, Uncontrollably, and so forth)
Data set worker establishment/setup, replication, and the board (SQL Worker, MongoDB, Redis, MySQL, and so forth)
Worker Information Movement
Mail Worker Arrangement/Setup and the board
Worker Security and checking
0 notes
Text
How to use yum to install MongoDB 4.0 on CentOS 8 Linux
How to use yum to install MongoDB 4.0 on CentOS 8 Linux
[ad_1]
MongoDB on CetnOS 8 or Stream Linux or on any operating system is meant to provide a highly reliable and scalable enterprise database. MongoDB is called a document type database and can store JSON etc.
The commands given below are to install and perform initial settings of the latest version of MongoDB; on the CentOS 8 Linux / stream or RHEL 8server environment, however, it will also…
View On WordPress
0 notes
Text
Rocket.Chat Installation Process(centos)
Rocket.Chat in CentOS STEP 1- Install necessary dependency packages
Update package list and configure yum to install the official MongoDB packages with the following yum repository file:
sudo yum -y check-update cat
View On WordPress
0 notes
Text
In this guide, we will take you through the steps to Install Graylog on CentOS 8 / RHEL 8 with Elasticsearch 7.x and MongoDB 4.x. Graylog is an open-source log management system that allows System Administrators/Developers to aggregate up to terabytes of log data, from multiple log sources. It is highly scalable to fit any Infrastructure. Graylog comes with an intuitive UI, fast and powerful search feature, alerting and reporting. It lets you group systems into streams for ease of log searching and proper management. Graylog UI is simple and intuitive with complete user management and support for LDAP. Similar articles: How To Forward Logs to Grafana Loki using Promtail Install Graylog 4.x on CentOS 8 / RHEL 8 Linux Graylog requires Java, Elasticsearch, and MongoDB. Elasticsearch is responsible for logs storage. We will begin with the installation of the dependencies then Graylog. Note: This is a single server installation of Graylog on CentOS 8 / RHEL 8. For multi-cluster setup, consult official Graylog documentation. Step 1: Configure SELinux If you’re using SELinux on your system, set the following settings: sudo yum -y install curl vim policycoreutils python3-policycoreutils sudo setsebool -P httpd_can_network_connect 1 sudo semanage port -a -t http_port_t -p tcp 9000 sudo semanage port -a -t http_port_t -p tcp 9200 sudo semanage port -a -t mongod_port_t -p tcp 27017 Step 2: Install Java on RHEL / CentOS 8 As Elasticsearch depends on Java 8, you need it installed on your system prior to installing Elasticsearch RHEL 8 / CentOS 8. sudo yum install java-11-openjdk java-11-openjdk-devel Confirm Java installation: $ java -version openjdk version "11.0.14.1" 2022-02-08 LTS OpenJDK Runtime Environment 18.9 (build 11.0.14.1+1-LTS) OpenJDK 64-Bit Server VM 18.9 (build 11.0.14.1+1-LTS, mixed mode, sharing) Step 3: Install Elasticsearch 7 on RHEL 8 / CentOS 8 Add Elasticsearch repository: cat
0 notes
Text
CentOS Web Panel Kurulumu
CentOS Web Paneli, (Dedicated ve VPS) sunucuların hızlı ve kolay yönetimi için tasarlanmış ücretsiz web hosting kontrol panelidir. Bir şeyler yapmak istediğiniz her seferinde SSH konsolunu kullanmanız için gereken işleri ve işleri azaltmak için çok sayıda seçenek ve özellik sunar. Deneme amaçlı olarak 10'un üzerinde ücretsiz web kontrol paneli denedim (Webmin ve Virtualmin daha denemedim). Sonuçta en stabil ve en işlevsel olanı CWP olarak kararlaştırdım. Sonradan gelen düzenleme: Bir üstteki paragrafta CWP en iyisi demiştim fakat bugün Ajenti'yi kapsamlıca denedim. Şu anda kararımı değiştirdim. Ajenti CWP'den daha iyidir. CentOS Web Paneli Kurulumuna tıklayarak özellikleri geçip direkt kuruluma başlayabilirsiniz.
CentOS Web Panel Özellikleri
CWP otomatik olarak istenen sunucunuza tam LAMP yükler: Apache, php, phpmyadmin, webmail, mail sunucusu... CWP Kurulumu Sırasındaki Özellikleri Nedir? - Apache Web Sunucusu (Mod Güvenliği + Otomatik olarak güncellenen kurallar isteğe bağlı) - PHP 5.6 veya 7.0(suPHP, SuExec + PHP sürüm seçici) - MySQL / MariaDB + phpMyAdmin - Postfix + Dovecot + roundcube web postası (Antivirüs, Spamassassin isteğe bağlı) - CSF Güvenlik Duvarı - Dosya Sistemi Kilidi (tüm dosyaları kitleme) - Yedeklemeler (isteğe bağlı) - Sunucu yapılandırması için AutoFixer Diğer Uygulamalar (sonradan eklenebilir) - CloudLinux + CageFS + PHP Seçici - Softaculous - Komut Dosyası Yükleyicisi (Ücretsiz ve Premium) - LiteSpeed Enterprise (Web Sunucusu)
Web Sunucusu Özellikleri
- Varnish Önbellek sunucusu (sunucu performanslarınızı üç kata kadar yükseltin) - Nginx Ters Proxy (statik dosyaları en hızlı şekilde almanızı sağlar) - LiteSpeed Kurumsal entegre - Apache'yi kaynaktan derler (performansı% 15'e kadar yükseltir) - Apache reCompiler + Tek bir tıklama ile ek modüller kurulumu - Apache sunucu durumu, yapılandırması - Apache Yönlendirme Yöneticisi - Apache vhost'larını, hayalet şablonlarını, yapılandırmayı içeriyor - Tek bir tıklama ile tüm apache Sanal konaklarını yeniden oluştur - suPHP ve suExec (geliştirilmiş güvenlik) - Mod Güvenliği: Comodo WAF, OWASP kuralları (tek bir tıklama ile kurulum, otomatik güncellemeler, kolay yönetim) - Tek bir tıklamayla Tomcat 8 sunucu yönetimi ve kurulumu - Yavaş Loris saldırılarından DoS koruması - Spam korumalı RBL korumalı Apache (HTTP PUT, POST, CONNECT'i koruma) - Perl cgi betiği desteği
PHP Özellikleri
- PHP kaynaktan derler (performanslarda% 20'ye kadar yükselir) - PHP Switcher (5.2, 5.3, 5.4, 5.5, 5.6, 7.0, 7.1, 7.x gibi PHP sürümleri arasında geçiş yapın) - PHP Seçici kullanıcı başına veya klasör başına PHP sürümünü seçer (PHP 4.4, 5.2, 5.3, 5.4, 5.5, 5.6, 7.0, 7.1, 7.x) - Basit php editörü - Kullanıcı panelinde basit php.ini jeneratörü - Tek bir tıklama ile PHP eklentileri - PHP.ini editörü & PHP bilgi & List modülleri - kullanıcı hesabı başına php.ini (/home/USER/php.ini dosyasında değişiklikler ekleyebilirsiniz) - FFMPEG, Video streaming web siteleri için) - CloudLinux + PHP Seçici - ioncube, php-imap ...
Kullanıcı yönetimi
- Kullanıcıları Ekle, Listele, Düzenle ve Kaldır - Kullanıcı İzleme (listelenen kullanıcılar açık dosyalar, dinleme soketleri ...) - Shell erişim yönetimi - Kullanıcı Limit Managment (Kota ve Inodlar) - Sınır İşlemleri: Hesap başına maksimum işlem sayısı. - Açık Dosyaları Sınırla: Her hesap için açık olan maksimum dosya sayısı. - Kullanıcı FTP ve Dosya Yöneticisi - CloudLinux + CageFS - Hesap başına ayrılmış IP
DNS Özellikleri
- FreeDNS (Ücretsiz DNS Sunucusu, ek IP'ye gerek yok) - DNS bölgeleri ekleme, düzenleme, listeleme ve kaldırma - Ad sunucusu IP'lerini düzenleme - DNS bölgesi şablonu düzenleyicisi - Yeni Kolay DNS Bölge Yöneticisi (ajax ile) - google (ayrıca rDNS, isim alanlarını kontrol etmek ...) kullanarak Ek çözünürlük bilgisi olan yeni DNS Bölgesi listesi
E-posta Özellikleri
- postfix & dovecot - Posta Kutuları, Diğer Adlar - Roundcube web postası Postfix Mail kuyruk yöneticisi - rDNS Kontrol Modülü (rDNS kayıtlarını kontrol edin) - AntiSPAM (Spamhaus cronjob) - SpamAssassin, RBL kontrolü, AmaViS, ClamAV, OpenDKIM - SPF ve DKIM Entegrasyonu - Postfix / Dovecot Mail sunucusunu (AntiVirus, AntiSpam Protection) yeniden oluşturun - E-posta Otomatik Yanıtlayıcı - E-posta Keşfedin, tüm posta kutularını bir konumdan okuyun. - Posta Yönlendirme (yerel veya uzak MX Eşanjörü)
Sistem Bilgisi Özellikleri
- Donanım Bilgileri (CPU çekirdeği ve saat bilgisi) - Bellek Bilgileri (Bellek kullanım bilgisi) - Disk Bilgisi (Ayrıntılı Disk durumu) - Yazılım Bilgisi (çekirdek sürümü, çalışma süresi ...) - Hizmetler Durumu (Hızlı servisler örneğin, Apache, FTP, Mail ... yeniden başlatılır) - ChkConfig Yöneticisi (Hızlı listeleme ve hizmetlerinizi yönetme) - Hizmetler İzleme (hizmetleri otomatik olarak yeniden başlatma ve e-posta bildirimleri) - Ağ bağlantı noktası kullanımı - Ağ yapılandırması - SSHD yapılandırması - Otomatik Düzeltici (önemli yapılandırmayı denetler ve sorunları otomatik olarak düzeltmeye çalışır) - Sysstat Grafikleri
İzleme Özellikleri
- Canlı İzleme (Monitör hizmetleri ör. Üst, apache istatistikleri, mysql ...) - Panelde Java SSH Terminali / Konsolu kullanın - Hizmetler Yapılandırması (örn., Apache, PHP, MySQL ...) - Ekran / arka planda kabuk komutlarını çalıştır
Güvenlik Özellikleri
- CSF Güvenlik Duvarı (En İyi Linux Güvenlik Duvarı) - SSL jeneratörü - SSL Sertifika Yöneticisi (SSL Sertifikalarının hızlı ve kolay kurulumu) - Letsencrypt, tüm alan adlarınız için ücretsiz SSL sertifikaları - CloudLinux + CageFS - CSF / LFD BruteForce koruması - IP erişim kontrolü - Mod Güvenlik + OWASP kuralları (tek bir tıklama ile kurulum, kolay yönetim) - Yavaş Loris saldırılarından DoS koruması (Apache için) - Dosya Sistemi Kilidi (daha fazla web sitesi hackingi olmaz, tüm dosyalarınız değişikliklerden etkilenmez) - PHP, komut dosyasının adını ve yolunu en iyi veya işlem listelerinde gösterir - Apache kullanıcı başına php işlem sayısını sınırlıyor - Otomatik Yedeklemeler - Sistem ve diğer kullanıcı süreçlerini gizle - SFTP Güvenliği - AutoSSL (yeni hesap, addon etki alanı veya alt etki alanı oluştururken otomatik olarak Letsencrypt SSL sertifikası yükleyin)
SQL Özellikleri
- MySQL Veritabanı Yönetimi - Yerel veya uzaktan erişim kullanıcıları ekleyin - Canlı Monitör MySQL işlem listesi - Oluşturun, Veritabanını kaldırın - Veritabanı başına ek kullanıcılar ekle - MySQL sunucu yapılandırması - PhpMyAdmin (veritabanı yönetimi) - PostgreSQL, phpPgAdmin Desteği - Uzaktan MySQL desteği (web sunucusundan mysql yükünü kaldırın) - MongoDB Yöneticisi / Yükleyicisi
Ekstra seçenekler
- TeamSpeak 3 Yöneticisi (Ses sunucuları) - Shoutcast Yöneticisi (Shoutcast akış sunucuları) - Otomatik güncelleme - Yedekleme yöneticisi - Dosya Yöneticisi - Scripts klasörü "/ scripts" 15+ betiğin üzerinde - Alan başına sanal FTP kullanıcıları - cPanel Hesabı Geçişi (dosyaları, veritabanları ve veritabanı kullanıcılarını geri yükler) - Torrent SeedBox (Deluge WebGU ile bir tıklama yükleyin) - SSH anahtar üreteci Ve diğer pek çok seçenek ...
CentOS Web Panel Kurulumu
Kurulum Öncesi Hazırlık
Herhangi bir sorun oluşmaması için, bu bölümün tamamını kurulum işleminden önce iyice okuyun. CentOS Web Panel yükleyicisinin başlatılmasından önceki gereksinimler: - Yalnızca statik IP adreslerini destekler. Dinamik, yapışkan veya dahili IP adreslerini desteklemez. - Bir kaldırıcı sağlanmaz. CWP'yi yükledikten sonra paneli kaldırmak için yeniden kurmanız gerekir. - Herhangi bir yapılandırma değişikliği yapmadan sadece yeni kurulmuş bir işletim sistemine CWP'yi yükleyin.
Sistem Gereksinimleri
32 bit işletim sistemleri minimum 512 MB RAM gerektirir 64 bit işletim sistemleri minimum 1024 MB RAM (önerilir) gerektirir Önerilen Sistem: 4 GB + RAM, böylece e-postaların Anti-virüs taraması gibi tam işlevselliğe sahip olursunuz. Sunucu Hazırlama CWP kurulumu için gerekli paketleri kuralım
yum -y install wget
Sunucu Güncelleştirmesi Şimdi sunucunuzu en yeni sürüme güncellemeliyiz
yum -y update
Sunucuyu Yeniden Başlat Tüm güncelleştirmelerin etkili olabilmesi için sunucunuzu yeniden başlatın.
reboot
Şimdi CWP Kurulumunu başlatmaya hazırsınız CWP yükleyicisi, 30 dakikadan daha uzun süre çalışabilir, çünkü apache ve php kaynaklarını derlemeye ihtiyaç duyar. Yükleyiciyi İndiriyoruz CentOS 6 için:
cd /usr/local/src wget http://centos-webpanel.com/cwp-latest sh cwp-latest
CentOS 7 için:
cd /usr/local/src wget http://centos-webpanel.com/cwp-el7-latest sh cwp-el7-latest
kodları satır satır sırasıyla giriyoruz. Sunucuyu Tekrar Yeniden Başlatıyoruz. Kurulum tamamlandı. Değişikliklerin kaydolması için sunucuyu tekrar yeniden başlatıyoruz.
reboot
CentOS Web Paneli Yapılandırması Sunucunuzdaki yükleyici tarafından sağlanan bağlantıyı kullanarak CWP sunucunuza giriş yapın. CentOS Web Panel Arayüzü Adresi: http://sunucu-ip:2030/ Kullanıcı adı: root Şifre: root şifreniz Şimdi bir web sunucusu barındırmaya hazırsınız.
0 notes
Text
Install MongoDB Community Edition on Red Hat Enterprise or CentOS Linux — MongoDB Manual 3.4
Install MongoDB Community Edition on Red Hat Enterprise or CentOS Linux — MongoDB Manual 3.4
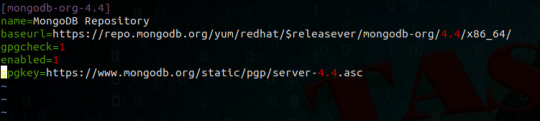
Configure the package management system (yum). Create a /etc/yum.repos.d/mongodb-org-3.4.repo file so that you can install MongoDB directly, using yum. Changed in version 3.0: MongoDB Linux packages are in a new repository beginning with 3.0. For the latest stable release of MongoDB Use the following repository file: Copy [mongodb-org-3.4] name=MongoDB Repository…
View On WordPress
0 notes
Text
Securing your MongoDB server
As I’m sure many of you know, there has been a massive amount of open MongoDB servers on the internet that have been discovered, and “hackers” have been taking advantage of this. Part of what makes these attacks so easy for “hackers” is that the tools are already there, just google “mongodb-tools” and you’ll see tools like mongodump, mongoexport, mongorestore, etc, as well as of course just the mongo shell. By leveraging these tools it’s incredibly easy for “hackers” to make extremely simple scripts to automate the process of dumping, dropping, and inserting a ransom note or in some cases, just dropping and inserting a ransom note.
Let’s get into how to protect against these kind of “attacks”. Now first of all, if you are running the MongoDB instance on the same server that your code that needs to access the MongoDB is running on, this is super easy. Just get a firewall (however you should still enable authentication, read further)! You should have one regardless. I recommend firewalld, as it’s super easy to use, works great, and is in basically every single distributions repositories. For CentOS 7/RHEL you can do:
sudo yum install firewalld # installs firewalld sudo systemctl enable firewalld # enables firewalld to run on boot sudo systemctl start firewalld # starts firewalld
There you go! Now if you need to run your MongoDB server on a server different than the one that is running your app itself, it’s slightly trickier, but still ridiculously easy, we just need to add authentication and a rule on who can access port 27017 on our MongoDB server. First, do the following in the mongo shell:
use admin db.createUser({ user: "<username>", pwd: "<password>", roles: [ "root" ] });
Now like with Regex, it’s best to be as specific as possible, so for example, if your application only needs access to the “production_memes” database, then just create a user that has the role: { role: “readWrite”, db: “production_memes” }, of course, you still should create a root user for yourself, just don’t use it in the application.
Then we make sure MongoDB is always started with authentication. Find your MongoDB configuration (for me it’s /etc/mongodb.conf) file and add the following line:
auth = true
Now since you can also start mongodb via the “mongod” command, we should add the following in our .bashrc in case we accidentally start mongod from bash instead of systemctl start mongodb:
alias mongod='mongod --auth'
Now to use the mongo shell as root and “login” we just do:
use admin db.auth("<username>", "<password>");
There we go! If you need to connect from mongoose for example, we would do:
mongodb://<username>:<password>@localhost:27017/<dbName>?authSource=admin
Remember to read the username and password from a file in another directory so that your application won’t accidentally expose it’s credentials if the source were to get leaked somehow.
Now let’s add the rule to our firewalld configuration to only accept traffic from the app’s main server:
firewall-cmd --permanent --zone=public --add-rich-rule=' rule family="ipv4" source address="<your app server IP address>" port protocol="tcp" port="27017" accept'
firewall-cmd --reload
Now I certainly did not cover all there is, so you should still check out the MongoDB Security Checklist. I hope this story taught you how easy it is to do these types of “attacks” and gave you a start on how to keep your MongoDB secure!
0 notes
Text
In this guide, I’ll take you through the steps to install Graylog 4 on CentOS 7|RHEL 7 Linux system. Graylog is an open source log management platform which enables you to aggregate up to terabytes of log data, from multiple log sources, DCs, and geographies with the capability to scale horizontally in your data center, cloud, or both. The Graylog search function is really fast and powerful, so you can group your servers into streams for easy log searching. Graylog UI is simple and intuitive with a complete user management and support for LDAP. It also has support for alerting and reporting. Graylog 4.x has full support for Elasticsearch 7.x and any latest version of MongoDB – 4.x. If you are an Ubuntu and CentOS 8 user, check: Install GrayLog on Ubuntu 20.04 / Ubuntu 18.04 Install GrayLog on CentOS 8 Graylog depends on Java, Elasticsearch, and MongoDB for its functions. Elasticsearch is responsible for logs storage and MongoDB is for storing Graylog related configurations. Step 1: Configure SELinux If you’re using SELinux on your system, set following settings: sudo yum -y install curl vim policycoreutils sudo setsebool -P httpd_can_network_connect 1 sudo semanage port -a -t http_port_t -p tcp 9000 sudo semanage port -a -t http_port_t -p tcp 9200 sudo semanage port -a -t mongod_port_t -p tcp 27017 Step 2: Add required repositories: Enable EPEL repository. CentOS 7: sudo yum -y install epel-release RHEL 7: sudo subscription-manager repos --enable rhel-*-optional-rpms \ --enable rhel-*-extras-rpms \ --enable rhel-ha-for-rhel-*-server-rpms sudo yum -y install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm Add MongoDB Repository: sudo tee /etc/yum.repos.d/mongodb-org-4.4.repo
0 notes
Text
In this guide we will perform an installation of MongoDB 5.0 on CentOS 8/7 & RHEL 8/7. MongoDB is a general-purpose, object-oriented, simple, and dynamic NoSQL database server used in developing modern dynamic apps. This implies that data objects are stored as separate documents in a collection unlike in traditional relational databases where rows and columns are used. MongoDB is written in C++ for massive scalability and flexibility which offers easy querying and indexing for developers. MongoDB offers both Community and Enterprise editions. The Community Edition is free for download while the Enterprise Edition is part of the Mongo Enterprise Advanced subscription. The Enterprise version has more features such as LDAP, Kerberos support, on-disk encryption, and auditing. Also, it includes comprehensive support for MongoDB development. MongoDB is available for Windows, macOS, and Linux Operating Systems and is supported by both 32 and 64-bit architectures. MongoDB 5.0 is the latest release version released on July 13, 2021. It has the following new features: Live Resharding Native time-series features for efficiently storing sequences of measurements over a period of time Multi cloud-security tools The Versioned API future-proofs your applications. Serverless database on MongoDB Atlas Seamless data redistribution Install MongoDB 5.0 on CentOS 8/7 & RHEL 8/7 Linux systems In this guide, we will walk through the installation of MongoDB 5.0 on CentOS 8/7 & RHEL 8/7 using the below steps. Step 1: Configure MongoDB YUM repository on CentOS 8/7 & RHEL 8/7 We need to create a /etc/yum.repos.d/mongodb-org-5.0.repo file to enable us install MongoDB 5.0 using the yum command. sudo tee /etc/yum.repos.d/mongodb-org-5.0.repo While in the shell, there are a number of activities you can do such as: 1. Create a User and Add Role in MongoDB Here we will create a user and give them admin roles. We will create and use the db “admin“ use admin db.createUser( user: "mongouser", pwd: passwordPrompt(), // or cleartext password roles: [ role: "userAdminAnyDatabase", db: "admin" , "readWriteAnyDatabase" ] ) Set the password for the user. Now exit the shell using. > exit bye Then login to the created user now. mongo -u mongouser -p --authenticationDatabase admin Enter the set password above and proceed. 2. List databases in MongDB To list existing databases use the command: > show dbs admin 0.000GB config 0.000GB local 0.000GB 3. Create a database in MongoDB. A new database in MongoDB is created by simply switching to a non-existing database and specify the name of the database. Let’s create a database named mongotestdb. use admin Sample Output: > use admin switched to db admin > 4. Create a collection in MongoDB With the database created, we can now add data to it. Below, we are creating a table for the user details. db.userdetails.insertOne( F_Name: "fist name", L_NAME: "last name", ID_NO: "12345", AGE: "49", TEL: "+254654671" ) Show the created table/collection show collections Sample Output: > show collections system.users system.version userdetails > 5. Create a User with read and write privileges. To create a user with read and write privileges in MongoDB use the syntax in the below commands: use testdatabase db.createUser( user: 'testuser', pwd: 'P@ssWord', roles: [ role: 'readWrite', db: 'testdatabase' ] ); Change MongoDB default Path on CentOS 8/7 & RHEL 8/7. MongoDB stores its data in the default path in /var/lib/mongo. You can set MongoDB to store data in a custom path as shown below. First, stop the service: sudo systemctl stop mongod.service Then create a new custom path to use to store MongoDB data. sudo mkdir -p /data/mongo Set the owner of the directory to mongod as below. sudo chown -R mongod:mongod /data/mongo Then modify /etc/mongod.conf to accommodate the new directories.
sudo vi /etc/mongod.conf Edit the paths in the file as below. path: /data/log/mongodb/mongod.log #where to write logging data. dbPath: /data/mongo #Where and how to store data. pidFilePath: /data/mongodb/mongod.pid # location of pidfile Configure SELinux and its enforcing mode since the path has been changed. Without configuring SELinux, it will not allow MongoDB to access /sys/fs/cgroup. First, install checkpolicy. sudo yum install checkpolicy ####OR### sudo yum install policycoreutils-python Create a new check policy with the information as below. cat > mongodb_cgroup_memory.te
0 notes
Text
MongoDB is a general-purpose, object-oriented, and dynamic NoSQL database server used in developing modern dynamic apps. In MongoDB, data objects are stored as separate documents in a collection unlike in traditional relational databases where rows and columns are used. It offers both the Community version which is free for download and the Enterprise version which is part of the Mongo Advanced subscription and has more features including; LDAP, Kerberos e.t.c MongoDB Compass is the official GUI tool for MongoDB that aids in creating, reading, updating, and deleting databases graphically. This eliminates the need of running Mongo commands for every task. It allows one to explore data, run queries and interact with the database with full CRUD functionality. MongoDB is a much better alternative for the Mongo Shell since you can do all the operations done in the shell and more such as: Get real-time server statistics. Manage indexes. Its extendable via plugins Visualize and explore data stored in the database. Understand performance issues with visual explain plans Validate data with JSON schema validation rules. With the above knowledge, we are set to begin this guide on how to install and use MongoDB Compass on CentOS 8/7 | Rocky Linux 8. Step 1: Download MongoDB Compass on CentOS 7/8 | Rocky Linux 8 Unlike MongoDB Database, the MongoDB compass is not available in the base repository of CentOS 8/7 | Rocky Linux 8 therefore we have to download it from the official website. This is done by visiting the Compass official download page and select the platform on the right side as shown below. For CentOS 8/7 | Rocky Linux 8 installation, we will select the RedHat package and download the .rpm file. Alternatively, you can download the stable version of MongoDB compass on CentOS 8/7 | Rocky Linux 8 using Wget as below. First, you need to have Wget installed on your system. sudo apt install wget Then proceed and download MongoDB compass as below. By the time of documenting this guide, the latest stable version was 1.28.1 download it as below. cd Downloads wget https://downloads.mongodb.com/compass/mongodb-compass-1.28.1.x86_64.rpm In case you want to download another version of MongoDB Compass, copy the download link on the official page and use Wget as above. Step 2: Install MongoDB Compass on CentOS 8/7 | Rocky Linux 8 On CentOS 8/7 | Rocky Linux 8 launch the terminal and navigate to the directory where you downloaded the .rpm file. If you used a browser, your download will go to the Downloads directory. Navigate to the directory and you should see the file below $ ls mongodb-compass-*.x86_64.rpm Now install MongoDB Compass with yum on CentOS 8/7 | Rocky Linux 8 Using the below command. sudo yum localinstall mongodb-compass-*.x86_64.rpm Dependency Tree: Dependencies resolved. ================================================================================ Package Arch Version Repository Size ================================================================================ Installing: mongodb-compass x86_64 1.28.1-1.el7 @commandline 100 M Installing dependencies: libXScrnSaver x86_64 1.2.3-1.el8 appstream 30 k mailx x86_64 12.5-29.el8 baseos 256 k ncurses-compat-libs x86_64 6.1-7.20180224.el8.1 baseos 327 k postfix x86_64 2:3.5.8-1.el8 baseos 1.5 M redhat-lsb-core x86_64 4.1-47.el8 appstream 44 k redhat-lsb-submod-security x86_64 4.1-47.el8 appstream 21 k spax x86_64 1.5.3-13.el8 baseos 215 k Transaction Summary ================================================================================ Install 8 Packages Total size: 103 M Total download size: 2.4 M Installed size: 455 M
Is this ok [y/N]: y Step 3: Run MongoDB Compass on CentOS 8/7 | Rocky Linux 8 To run MongoDB compass, navigate to the App Menu and launch it. It appears as below. With MongoDB compass launched, plugins will be loaded as shown. When plugins are loaded successfully, you will see this welcome window. Step 4: Connect to a MongoDB Database If you have a MongoDB instance installed on your system, you can connect to it by clicking connect as shown below. Alternatively, create a database using this guide Install MongoDB 5 on CentOS 8/7 & RHEL 8/7 You will be connected to the existing database on your system. Step 5: Connect to a Remote Database Instance If you want to connect to a remote database instance, click on “Fill in connection fields individually“. In the Hostname segment, you can connect to the localhost database or the remote system by entering its hostname. When done, click on connect. You should see your database as below. step 6: Create a database using MongoDB Compass While connected to a database, you can easily create and edit a database. In this database, let us create a database with the name mongotestdb and a collection with the name “user details“. Click on create database while on the above page Click on “Create Database” and you should see your database appear as below. Now we go into the database by clicking on it. In our created collection, we will try and add data to it. First, click on it to open. While on the above page, you can manually add the data or import data from your documents, normally a JSON or CSV file. Browse and load it, then select the type of file uploaded and click import. To create a file manually, click on “Add data” and select “Insert Document” on the drop-down list shown. You will enter details for your collection in the area paste one or more documents. Leave the Id as it is and click insert. You should have your collection added. Step 7: Drop a database in MongoDB Compass. You can easily delete a database in MongoDB compass by navigating to the database on the left and click drop database as shown Exit, disconnect from an instance in MongoDB compass by clicking on the connect button on the far left corner and select disconnect as shown. Conclusion. We have come to the end of this guide on how to install and use MongoDB Compass on CentOS 8/7 | Rocky Linux 8. We have seen how MongoDB compass aids one to easily create, edit and delete a database without using the shell commands. I hope this guide was helpful.
0 notes